Protect your Passwords.
1
%
encrypt
1
%
cyber
1
%
secure
Among the technologies assimilated by Comda are:


What is Vault?
HashiCorp Vault 0.1 technology is based on software for installation on workstations and enterprise servers. When done, a user can be created and logged in using a dedicated key and root token.
Once signed in, you can start building organizational secrets and determining who you want to participate in: From simple secrets like secure password storage, to creating a collection of identities that can be given to managed users.
For example, a developer who uses an application on Kubernetes under Google Cloud that connects to GitHub that connects to any database, e.g. in Microsoft AD, in order to replicate to AWS.
With Vault
Your secret is secure and work processes are effective.
Practic
- Download Vault login keys when installation is complete.
- Efficient and smart management of all Web passwords.
- Build an entity array that when operated, it can enter the user to some user/password websites, one after the other, granting restricted permissions from different kinds.
- Create a secure and efficient password management infrastructure.
Performing restrictive manipulations with confidential Web information
- Login time restrictions,
- Time constraints dedicated to presenting the information.
- Build a user identity set to create an efficient Workflow.
- Providing enhanced access to unauthorized employees and entities in need to access data.
- Starting with version 0.10: Microsoft Active Directory access is easily accessible.
Dedicated plugins can be downloaded for access to all identity providers
We help you to secure & management your organization passwords.
Comda has developed a system that allows central management and security of access to all the “secrets” of the organization such as passwords for access to various systems, certificates, API keys and the like. The Vault provides a strong layer of protection and identification for various systems. With the Vault you can manage and configure, in a central and uniform interface, all the secrets required to access various systems such as databases, APIs for third parties and the like. In addition, you can configure who heads to access each secret so that Vault reveals to each user only the secrets he is allowed to have.
All sensitive information of the organization is encrypted and protected by the Master key that is created when the Vault system is set up.


Vault Interfaces.
The Vault can be operated using two different interfaces:
• Rest API – Any action supported by the Vault can be done using API request \ response. You can define for each user which API Method it is allowed to run.
• Portal – Reveals a convenient user interface for password management and additional operations.
Authentication Methods.
The Vault system supports various identification methods such as: Kerberos identification, Radius server, PKI and more. Each type of identification is translated and saved as Entity in Vault. For each Entity, a Policy can be defined for which secrets can be accessed, for example, which database a user may access and what actions he may perform.
Documentation of operations and faults - Audit.
The system records to all logs all requests sent to it to perform such actions as: what user did authentication and what kind of identification, what secrets it accessed, what user changed password and etc. This information, along with the fault documentation, was written to SYSLOG and log files in various formats.
Vault Benefits and Different Uses.
Ability to convert type identification.
The Vault allows identification of a particular system with a different identification type of the identification that the system allows.
Contact for a uniform interface that allows access to different systems.
Instead of saving different credentials for different services or systems, Vault appeals to the service / system session and returns the token / session id to the access applicant.
Centralized management of secrets.
Changing the credentials for a particular system A to which N clients access does not require a change in N locations. The Vault credentials can be configured and managed in System A, centrally and sweep to all N clients.
Encrypt data in transit.
Encryption keys can be generated and configured using policy who can encrypt and who can decrypt. Useful in cases of requesting information encryption from an app using the Rest API
Secret Storage.
The Vault can store various secrets such as: environment variables, API keys, database credentials and more. This allows you to contact a vault uniform interface to access information instead of going to a number of different places such as plaintext files, databases, and the like. All secrets are kept encrypted.
The secrets are not revealed to the user.
The user who applies to Vault and requests access to a particular system does not know the credentials, for example, what is the password to access the system
Set up access for a limited time.
Creating temporary users in the database, changing passwords in AD, creating certificates (X509) with a short life cycle.
Possibility of keeping sensitive secrets in HSM.
Creating temporary users in the database, changing passwords in AD, creating certificates (X509) with a short life cycle.
Encrypt secrets stored outside the Vault repository.
The Vault is used, among other things, to encrypt and decrypt information. Applications can send a request to Vault to encrypt or decrypt information and store the encrypted / decrypted information in the same database with which they work.
Example of using Vault.
• Strong Vault Identification with Signer-1: A user directly accesses via the Vault API and requests access to the Singer-1 underwriting system. The underwriting. In this way, information security is maintained because the user does not know his / her password to Signer-1. (By the same token, strong OTP identification can be performed so that the user does not know the seed).
• Conversion Identification Type – The Vault enables identification with the example Wesign system, which currently allows identification using only a username and password, using another identification type such as AD or OTP. The user can contact Vault through AD for example, and the Vault with which Credentials is stored for Wesign will create a token identification for wesign without revealing the password to it.
Comsign Encrypt – a comprehensive data protection platform.
Comsign Encrypt enables organizations to easily protect sensitive data transmitted in any application, database or file. The system enables compliance with regulations – a unified solution for PCI, HIPAA, PII, etc. With the platform, organizations can protect their files without changes to the software code
Easy to implement and deploy
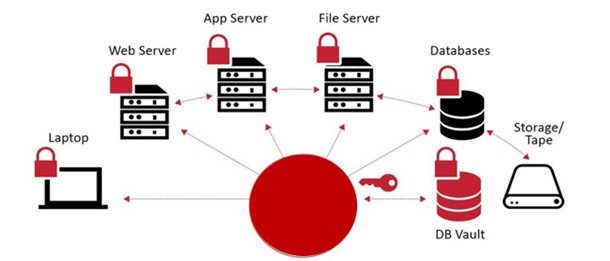
Comsign Encrypt is designed to seamlessly integrate into the existing enterprise infrastructure and involves only minor changes to the network that will hardly be noticed. Installation takes place within minutes and does not affect business processes. It provides an end-to-end encryption solution which can encrypt the below:
- Laptop/desktop
- File servers
- Web/app servers
- Database servers
And any structured and unstructured data.

Advantages of the Comsign Encrypt system.
• Reduce operating costs • Reduce risks by enforcing a security policy when using cloud, and outsourced employees • Reduce compliance costs – reduce traces using a “data exchange” policy
Easy to Use.
With Comsign Encrypt end users do not need to change their behavior in order to secure their files. The system is designed to also be adopted and used by non-technical users with minimal training only. • Transparent and non-intrusive to end users • No noticeable performance impact • Uses familiar Windows or Linux systems and commands • Non-technical staff can implement and enforce cyber security policies
Comsign Encrypt – Solution’s Architecture.
Comsign Encrypt is a software-based solution comprised of the below main components: • DPM File – enables encryption and access control of files, folders, applications, databases stored on laptops, desktops and servers. • DPM Token Manager – tokenizes, encrypts and anonymizes data using a web service interface. Allows creation of masking rules for unauthorized users. • DPM Key Manager – provides a central place for key management. Allows generation of keys internally or via an HSM. • DPM Database Manager – allows the masking of data stored in columns within databases. Integration with DPM Token Manager extends its features to tokenization, encryption and anonymization.


Flexible Key Management.
Comsign Encrypt Key Manager provides a flexible key management system to manage encryption keys on the cloud or on premise. Organizations are free to choose between a software-based key generation and a hardware one, such as HSM. Furthermore, they are not dependent on one HSM type or vendor as Comsign Encrypt offers a multi-vendor HSM support.


About
- About Us
- Case Study
- Articels
- News
- Careers
- List Item

